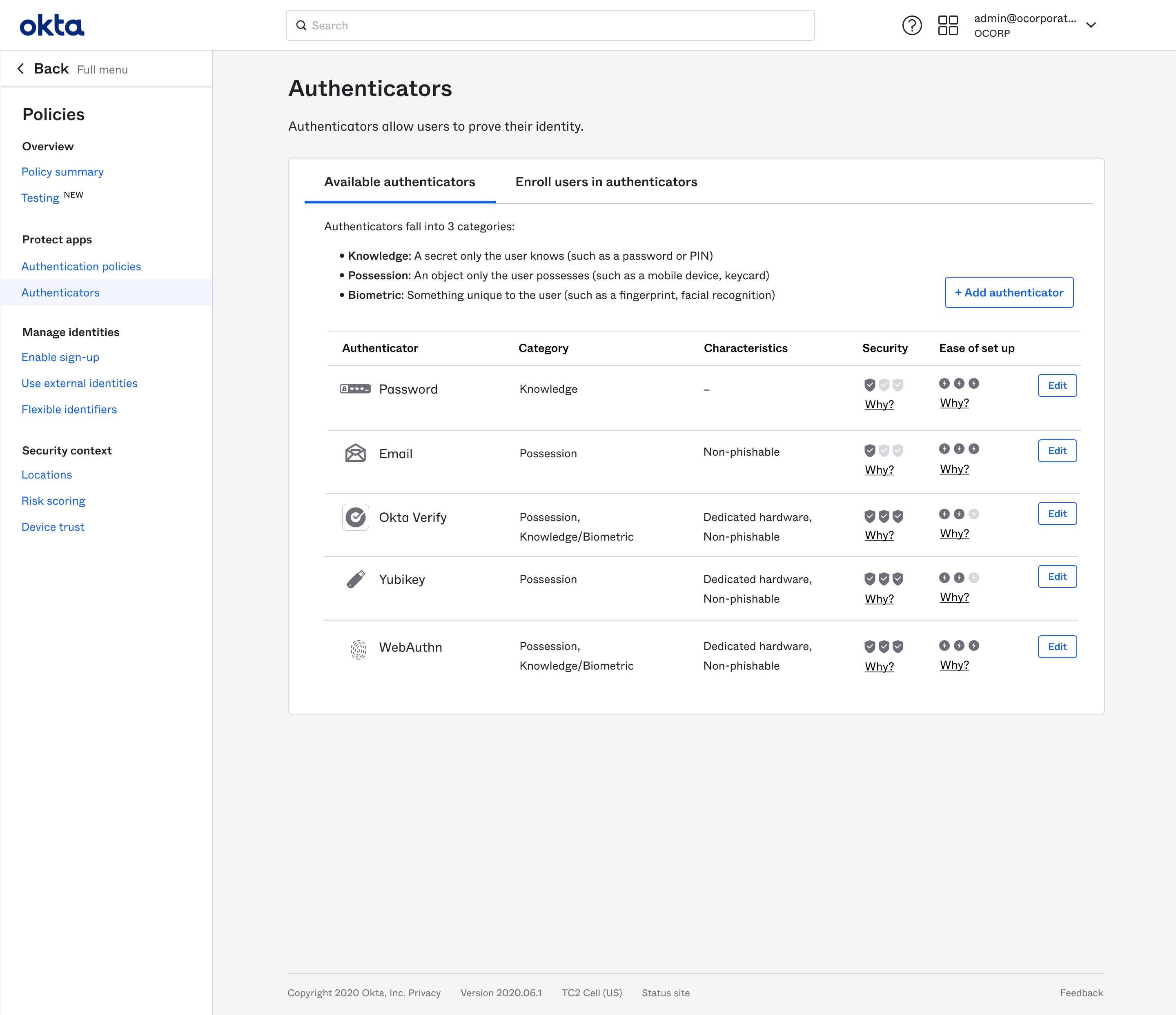
Old UI
Most of the pages looked something like this
Reduce complexity and risk for customers
Did research, created requirements, led design process, proposed roadmap items to leadership
I had observed anecdotally that our system was very difficult to understand and use. The most problematic area seemed to be Access Management. The set of settings and policies that governed how resources were protected and accessed spanned 13 pages across 3 different areas of the nav.
Most of the pages looked something like this

I knew that I didn't know enough to define a clear problem statment, let alone propose solutions. I needed to learn more about how customers thought and worked. I set a goal to better understand customers' goals and internal processes as well as their biggest pain points in using our existing product for Access Management.
With another designer and a researcher, I began a generative research process.
We learned that customers primarily care about security level and user friction. Neither was currently easy for them to control.
This was problematic because a mistaken setting could open up unauthorized access to protected personal data, corporate confidential data, or critical company infrastructure. It could also block authorized access, preventing all of a company's customers from interacting with their products or preventing all of a company's employees from being able to work.
According to account managers, this was decreasing feature adoption and customer sentiment.
My design partner and I presented these findings to Product team leadership. We got buy-in that there was a problem and we were given resources to find a solution and make a proposal.
We wanted to include broad expertise and build cross-functional buy-in. To do this, we led a series of design workshop sessions with stakeholders from 6 functional areas. With this group, we arrived at a set of strategies and a set of tactics for achieving them:
We had put the resulting design through 6 rounds of user testing including both customers and non-customers across our primary customer segments.
The solution was a comprehensive 3 year vision. It updated all of the settings for Access Management, addressing all 3 of the strategies (and all 6 tactics) outlined above. It also included incremental steps for achieving the vision.
The story we told and the videos we made of customer reactions were compelling. We were able to get a v1 added to the proper teams' roadmaps immediately. This includes a basic testing tool and a landing page that centralizes the navigation for Access Management. Then we began working with the Admin Experience team to design UI components and guidelines to enable other feature teams to add similar guidance and defaults across the product.
A testing tool shows all the system behavior outcomes and links off to the specific settings causing them. It also shows the resulting user experience for each state in an interactive sandbox.
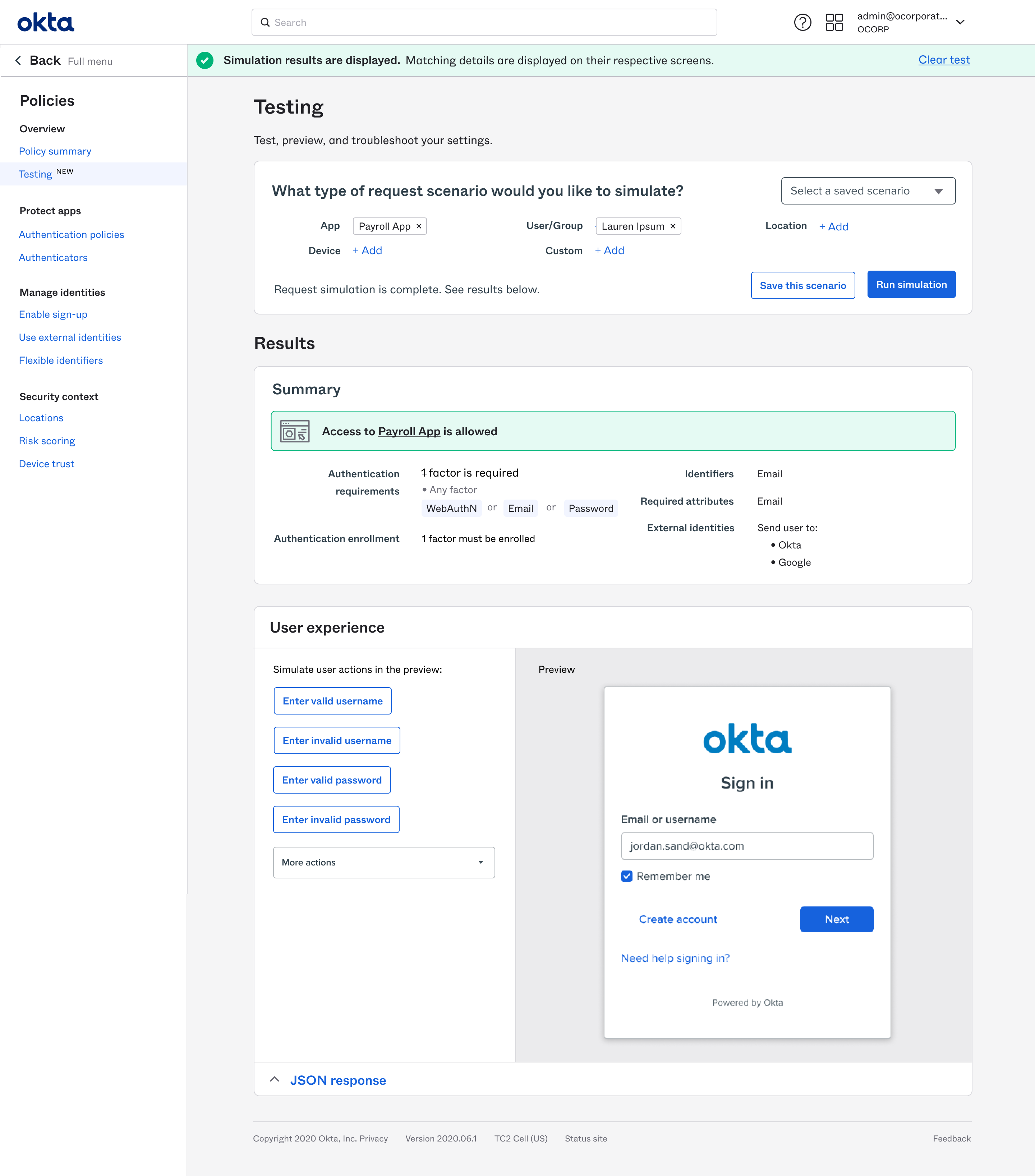
In addition, we built in a testing mode to every setting.
In test mode, all changes are staged and tested before being deployed.
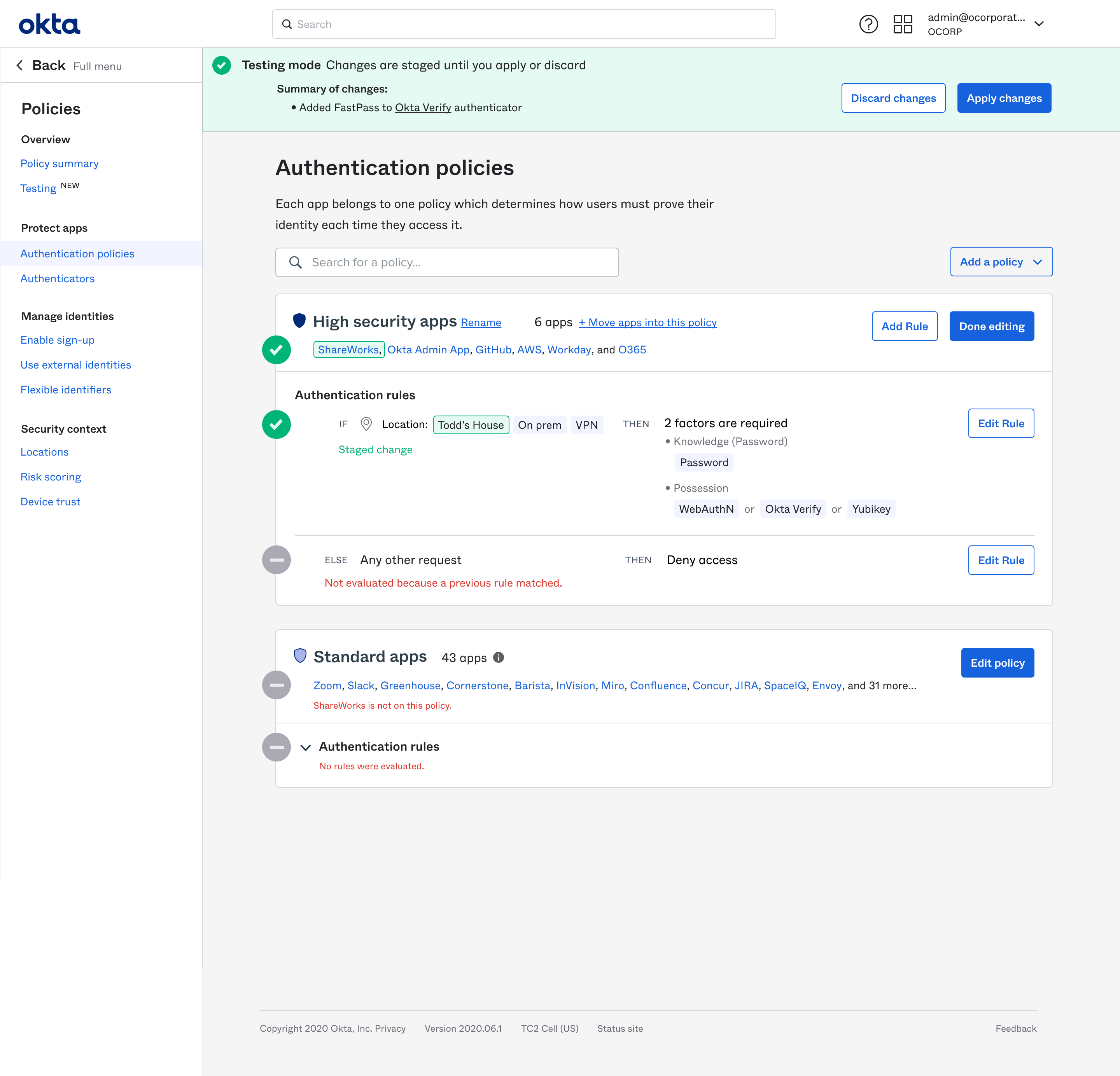
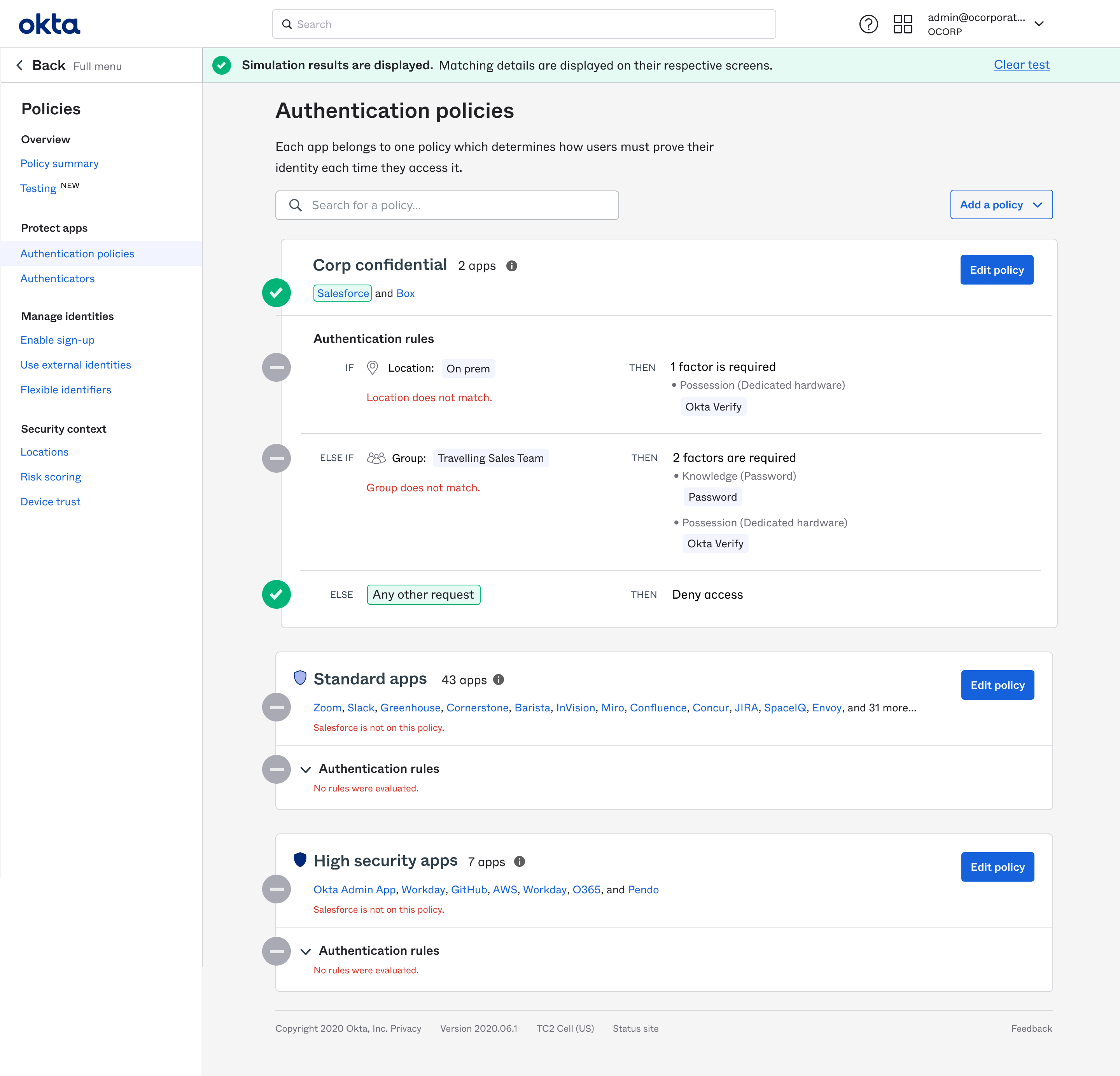
We made a landing page that centralized all the Access Management settings and showed their relationships to each other in terms of customer goals.
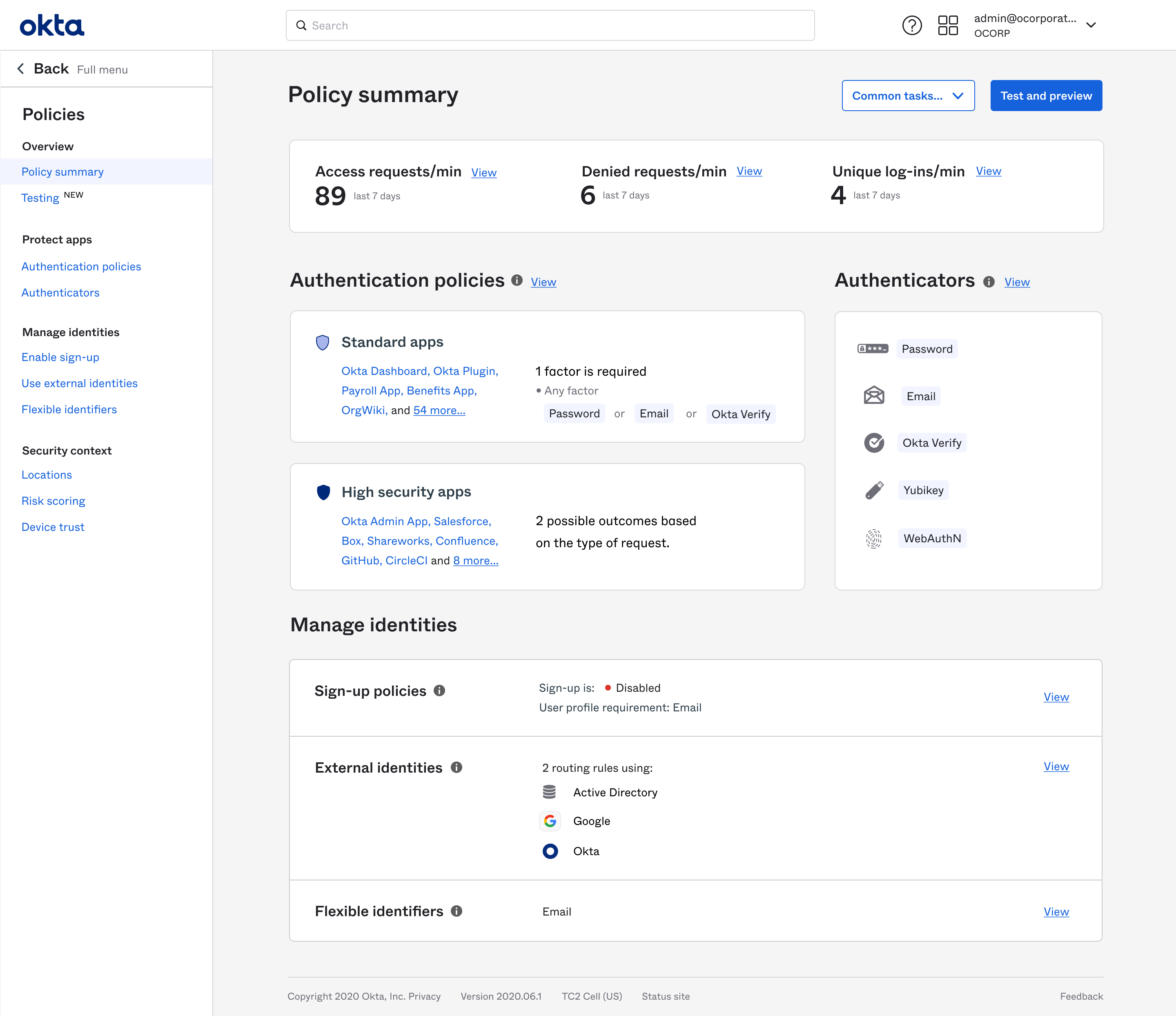
In each location, we surfaced and linked to the relevant related information. Here, a protected resource shows how all the high level system functions relate to it.
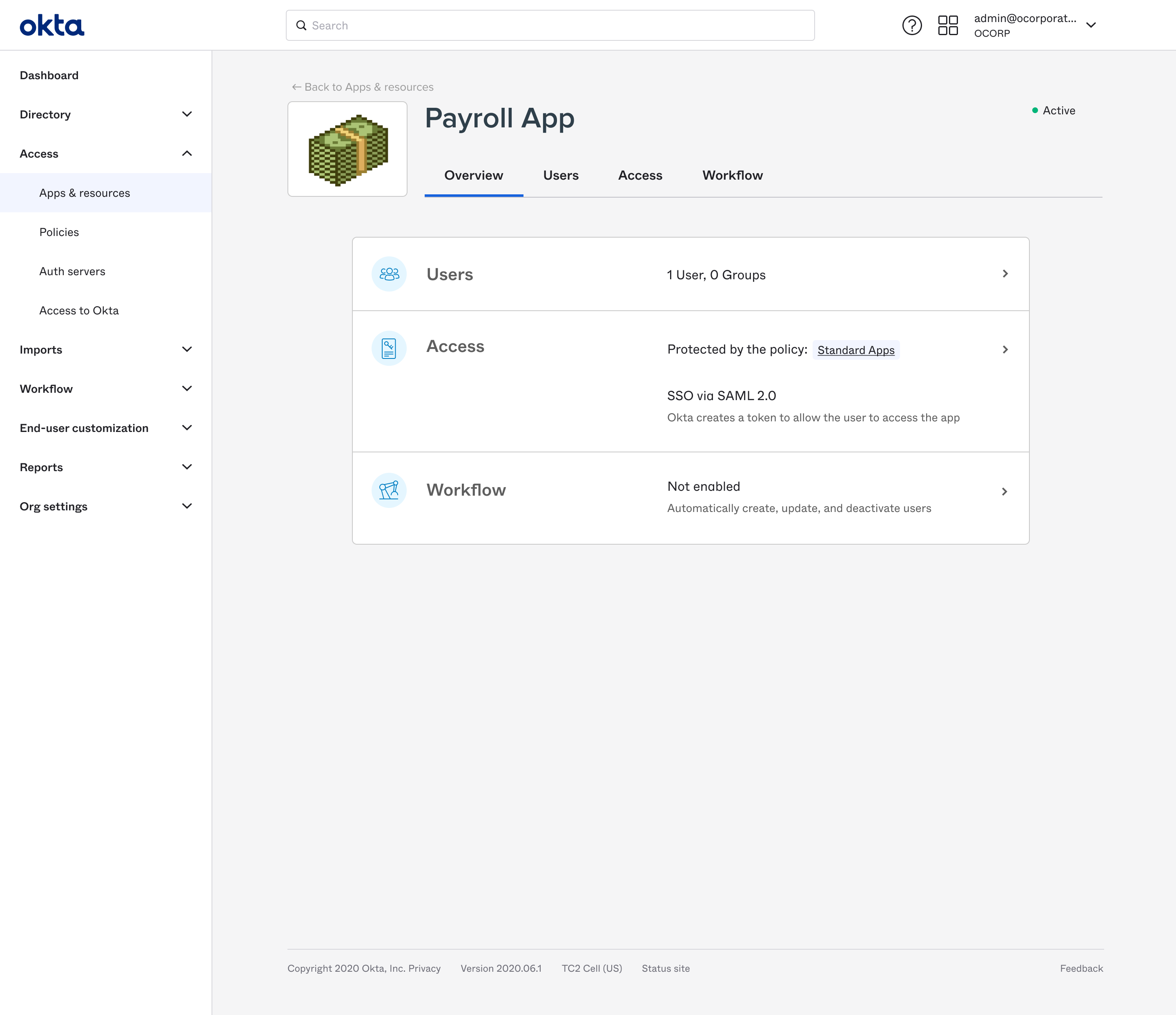
Clicking into the Access function, all the important settings impacting this resource are shown and linked.
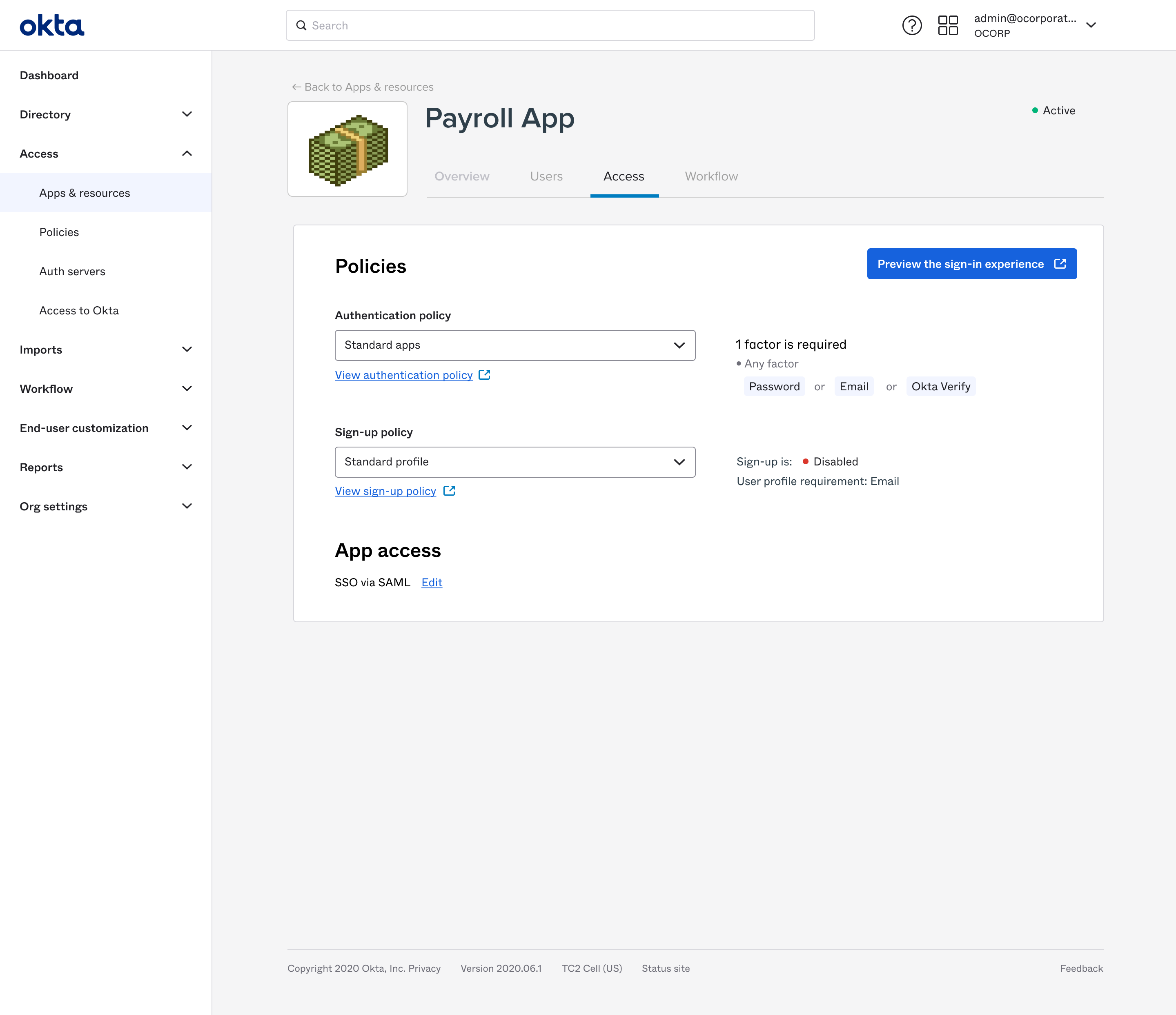
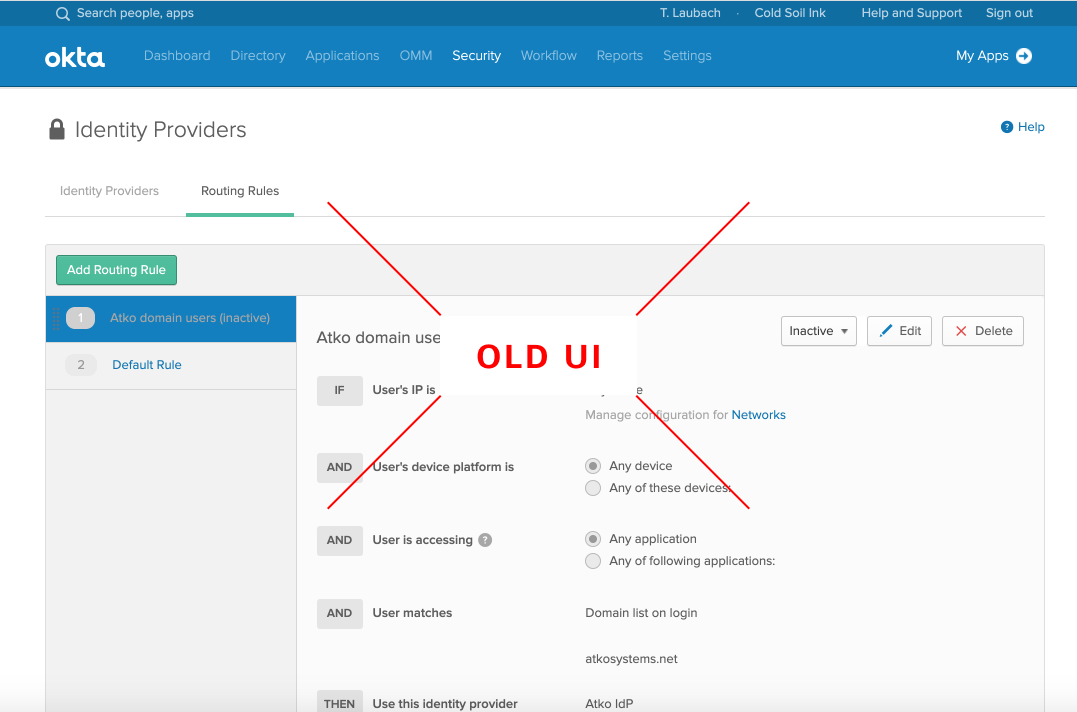
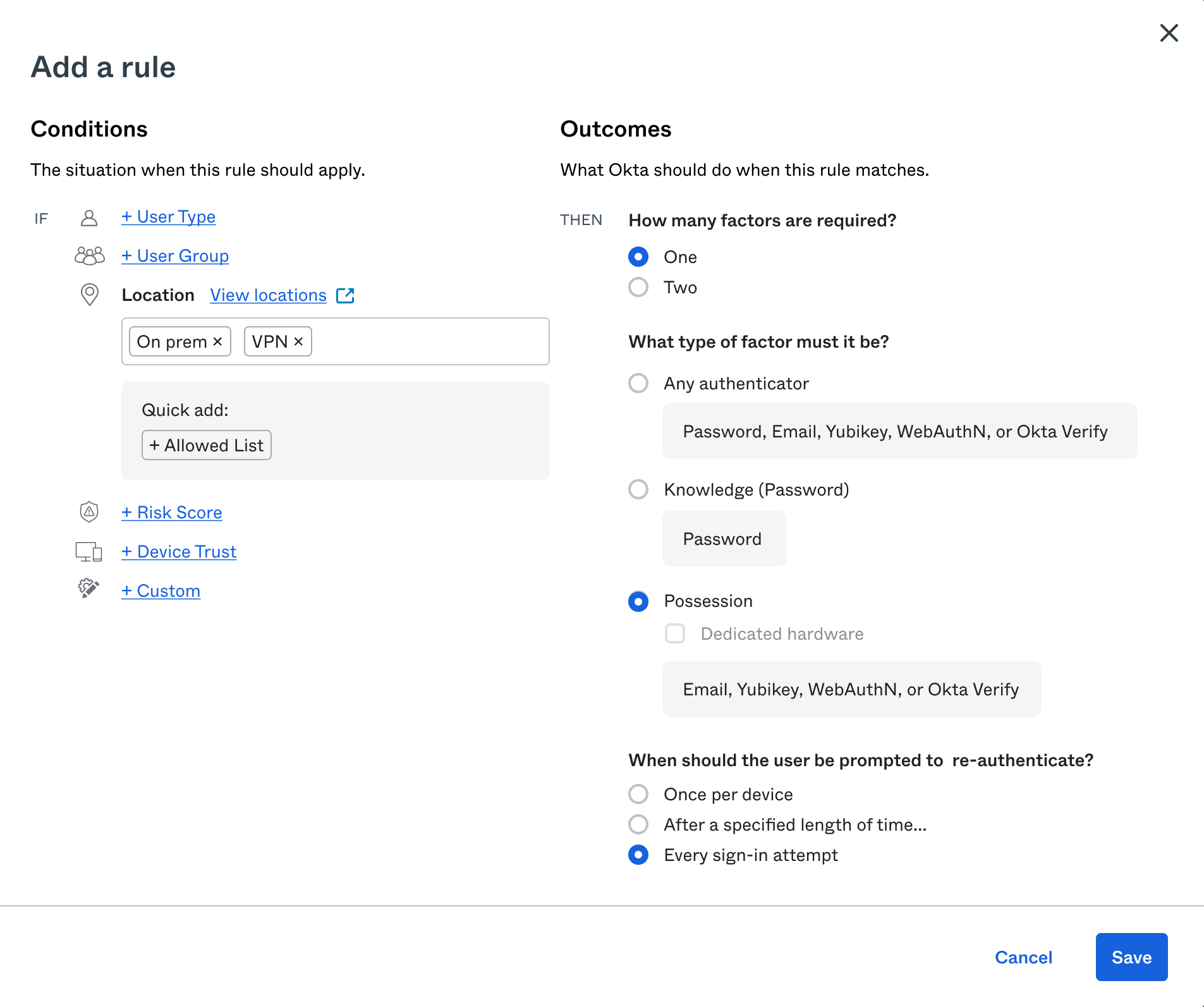
All settings are now in written in terms of the primary customer outcomes: security and UX. In this setting, each radio option shows both its security impact (which factor types would be required) and its UX impact (which authenticators a user can authenticate with).
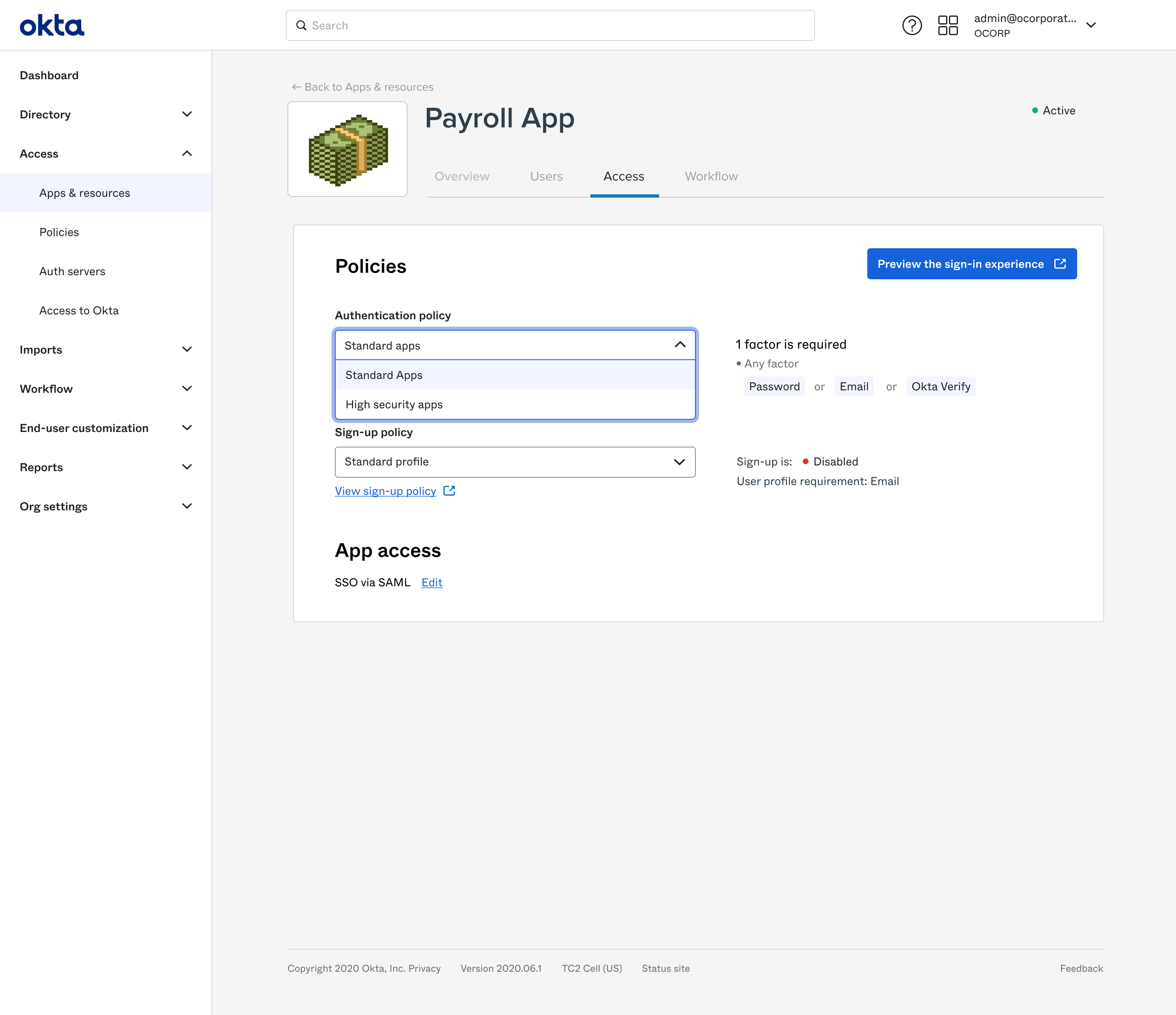
Built in defaults provide a lot of benefits.
Here, an instance starts with two default policies. A customer can easily pick the one they want for their first protected resource without having to dive in to the complexity of managing policies.
Built in guidance helps customers make informed and confident decisions. Here, the authenticators page helps admins understand the best framework for thinking about authenticators. Additionally, each authenticator provides guidance on the level of security and ease of use it provides.